Securing Networks
In the past, the hunt was on for natural resources and raw materials. This hunt turned at times very ugly, but now there is a new game to be hunted: raw data. Almost the whole world is wired and private citizens are conducting their affairs, from birth to death, through the networked world. Corporations and governments place their trust increasingly on the safety and reliability of the globally crisscrossing networks. But, as they say, knowledge is power and power allures those who would gain it by any means necessary, even in this new age.
According to research, the Finnish networks are one of the most cleanest in the world. This does not mean, however, that we could get complacent and smug. Criminals and even governmental actors are forever on the lookout for vulnerabilities and weaknesses in the software and the network itself. Their goal is usually monetary gain but recently a new trend can be seen. This so called hybrid warfare aims at influencing the workings and politics of foreign nations. The most egregious examples of this are fake-news websites, which harbor a clear political agenda, and the ongoing investigations in the United States into the alleged operations by Russia or Russian minded crackers in order to influence the 2016 presidential elections.
In addition to these headline-grabbing instances, the issues and questions pertaining to cybersecurity and cyber threats reach into the lives of ordinary people. No doubt, many still remember the so-called “Nigerian prince” scams which were prolific at the start of the millennium or the different “phishing” software that aim to acquire the unsuspecting person’s identity records and other information through malware and other tactics. As one might imagine, corporations and companies are feverishly pondering the issues of cybersecurity, and for good reason. Let us imagine for a second how serious of a crisis could be conjured up if, for example, the banking sector was the target of a coordinated and efficient cyber-attack. Payments would cease, the exchange of information would stop, and the confidential client records and information could be leaked either to the public or sold to the highest bidder on the underbelly of the Internet, the so-called Dark Web.

In order to prevent criminals and others malicious actors from disrupting the vital networks, a center for the study, testing, and defense against attack vectors has been set up in Jyväskylä in 2011. The JYVSECTEC Center was funded in 2011 with the objective of enhancing and improving the leading cybersecurity research, development, and training center in Finland.
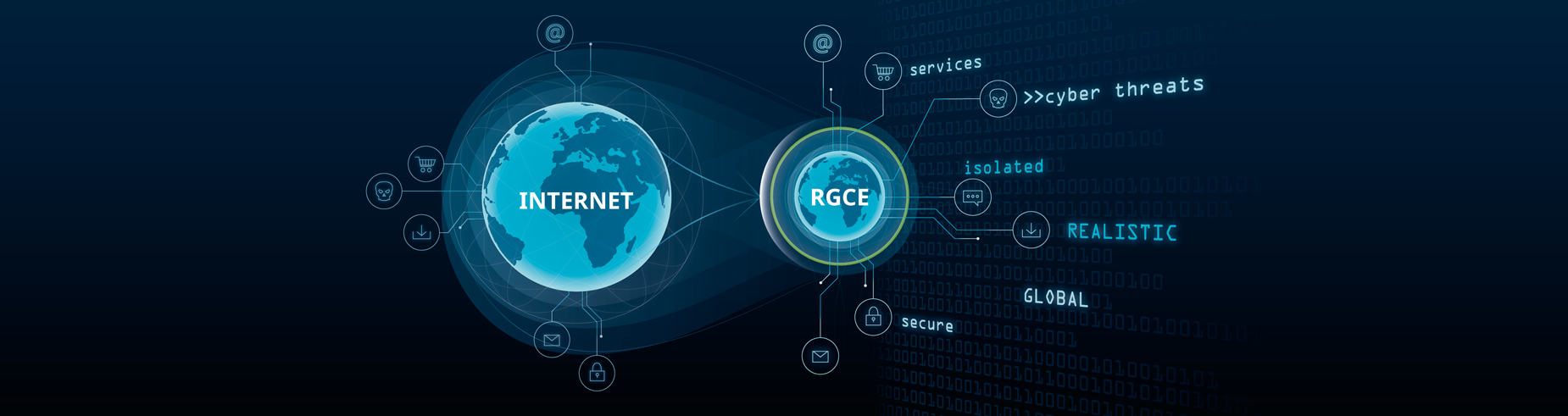
The JYVSECTEC Center and JYVSECTEC Center RGCE (Realistic Global Cyber Environment) projects aim at improving the cooperation between corporations, governmental actors, and JYVSECTEC Center, in addition to enhancing the Center’s functions. Through the projects, a “situation room” has been built at the Jyväskylä University of Applied Sciences. The companies and other actors use the room in cybersecurity exercises. The operations and procedures conducted by JYVSECTEC have been noted and praised across a broad spectrum, which include the Ministry of Defense, the Finnish Defense Force, and a multitude of corporations. For example, the Finnish Security Committee mentions in their implementation program for the national cybersecurity strategy the commendable actions done by the JYVSECTEC Center. In addition, the RGCE has been noted on the international level as having the widest applications and features of the various Cyber Ranges in Finland. This ensures that the RGCE will have great opportunities to improve the field of cyber security.
”There is a constant stream of new malware and viruses which means that the greatest challenge involves keeping ourselves ahead of the curve. For this to happen, we have to be able to maintain our expertise and experts.” -Mika Karjalainen
Contrary to the global trend, the RGCE in Jyväskylä is one of the few independent, non-military Cyber Ranges in the world. In addition to the independence of the RGCE, its operations include an exceptionally wide array of operational environments. According to Mika Karjalainen, the director of the IT-institute in the Jyväskylä University of Applied Sciences, the exploits and undertakings of JYVSECTEC, which include teaching, cooperation with various companies, and the participation in the national cyber defense exercises, can be further developed and broadened owing to the wide array of opportunities offered by the RGCE.
The JYVSECTEC Center aims to apply the scientific and academic knowledge and data generated by the universities and companies in its RGCE Cyber Range. Tero Kokkonen, as the senior lecturer and program manager at the IT-institute, reveals that inside the RGCE’s hood is a simulated environment modeled after the “real” Internet. In the simulated environment, the data packages are zipping through as though they were situated in the Internet we all know. The only differences between the simulacrum and the real is the scale, with the former having less traffic.
“Within the RGCE we can simulate user traffic, for example e-mails, Web-browsing and the use of video services which enhances the realism when we are testing and researching different threat vectors. Realism in this context means also that we can easily create the networks and environments of our partners or clients,” Kokkonen explains.
The IT-institute in Jyväskylä is engaged in collaboration with the University of Jyväskylä, and other institutes of higher learning throughout the country. This, Kokkonen emphasizes, is vital in a country as small as Finland.
“Out cooperation with the universities is mutually beneficial because, from the very outset, we have each have differentiated objects. Whereas the universities are focusing on basic academic research, the function of the universities of applied sciences is more practically oriented research and development activities. In this context we can utilize the RGCE in the R&D field with the other research institutes,” Karjalainen describes.

Bit Wars
In addition to working with companies, the RGCE has also been used to evaluate and demonstrate the capabilities of various socially critical actors, ranging from the electric grid to the armed forces. For example, in 2016 the RGCE played a critical role when the National Cybersecurity Exercise was conducted by the Ministry of Defense, Ministry of Finance, and the Finnish Defense Forces C5 Agency. The exercise simulated different attack, defense, and crisis scenarios. JYVSECTEC was also a participant in the 2017 exercises.
“The purpose of the RGCE is to conduct cybersecurity tests for clients and partners. With the tests, we are looking for weaknesses in the networks and services which the criminals and other actors might abuse in the real network environment,” Karjalainen describes.
The cyber exercises are linked tightly to the national cybersecurity strategy, which is of great interest to the JYVSECTEC Center.
The cyber domain should also be seen as a possibility and a resource. A safe cyber domain makes it easier for both individuals and businesses to plan their activities, which in turn boosts economic activity. A properly working environment also improves Finland’s appeal for international investors. In addition to these, cyber security itself is a new and strengthening business area. In addition to the increasing job opportunities and tax revenue, society accrues benefits from this strengthening business sector in many ways. National cyber security is interconnected with the success of Finnish companies.
-The Finnish Cybersecurity Strategy
“It’s good that there is a clear objective in mind, and that the different actors on the field and the various goals are all recognized on the national level. The strategy highlights the cooperation of the security services and it is great that the strategy acknowledges the special characteristic of the Finnish society,” ponders Karjalainen.
Cybersecurity, the tools it offers and the research conducted on them have been an important factor for the Jyväskylä University of Applied Sciences wherein students can study for the Master’s degree of cybersecurity, and have been able to do so since 2013 when it was the first to offer it in Finland. The university of applied sciences got another feather in its cap in 2016 when it was one of the founding organizations of the European Cyber Security Organization (ECSO).
Cybersecurity is hidden from the public, as long as it works, but when something goes awry, the problems can manifest themselves in our day-to-day lives. The so-called WannaCry cyberattack last spring targeted devices running on the Windows operating system. The data on the devices was locked beyond the reach of the users and held for ransom. Perhaps the most famous example of those who fell victim to the program was the NHS in the UK whose daily operations, and thus lives, were disrupted dramatically and, potentially, fatally.
The greatest single reason for why WannaCry was so far-reaching was that the users had not bothered to update their operating systems. This was also the reason why the damage done by the cyberattack was so limited in Finland.
“The Finnish ISPs and users have an elevated level of technological knowledge. In addition to this, the mentality prevalent in Finland is one of abiding by the rules, meaning in this case that the systems are updated quickly and often which partly helped in protection against the cyber-attack. There cultures where the systems are not updated so regularly faced the lion share of the attack and the damages it caused”, Karjalainen explains.
The greatest threats in the sector of cyber security come from criminal activities whose main motivations are money and power, Karjalainen says. Through digitalization and the development of the networks, the whole digital world is ours for the taking. This includes the criminal elements, too. The threats aimed at private individuals are different in nature from those aimed at companies and corporations as the latter ones can be the subject of espionage, which is not the greatest concern for private citizens.
National and international expertise
The core functions of JYVSECTEC include the organization of cyber security exercises, and teaching and educational activities. Of these, the most visible one is perhaps the exercise activities whose participants include a large number of companies, including the Finnish S Group and Telia, Kokkonen explains.
Some of the corporate clients do not want to have their cooperation with JYVSECTEC made public. This is because the companies do not want to become “honeypots” for the criminals who might set out to test the company’s defenses, and to prove their skills to others, Karjalainen describes. For other companies, the participation in the exercises and the security tests is an ace in the hole when it comes to branding, as through them the company can demonstrate that their networks are clean and trustworthy.
One of the corporations that has been participating in the project from the very beginning is Airbus DS Finland whose CEO, Vesa Arkko, credits the JYVSECTEC Centre activities, especially the training and networking activities it provides for the employees.
“For us, the main benefits of working with the JYVSECTEC Centre have been the testing opportunities and various education and training opportunities,” he continues.
He shares the assessment that the criminal cyberactivity has been on the rise but points out that it can offer the companies and corporations dealing with cybersecurity new business opportunities. According to Arkko, Finland is in need of a boost towards increasing the resources allocated to cybersecurity. This might not however happen without a major crisis that would show the people the importance of cybersecurity.
The specialists working at the JYVSECTEC Center have been able to further their own knowledge and skills through its activities, and to make sure that their skills are as sharp as the sector requires. The JYVSECTEC Centre and the IT-institute are educating their students to be the very best in cybersecurity, and are forever on the lookout to improve the know-how of their personnel, Karjalainen says.
“Through the projects we can produce regional know-how and jobs which ensure the region’s continued operations in the sector of cybersecurity”, he explains.
Another project that is closely linked to the JYVSECTEC Centre is the Finnish Cyber Security Certificate (FINCSC), which is aimed predominantly towards the SMEs. The goal of the project is to create a uniform cyber resilience test and assessment tool, which allows the issuing of certificates to the companies that pass the test. The certificate acts as a guarantee and as a testament that the level of cybersecurity within the company is deemed high.
“As citizens, we are extremely dependent of the SMEs”, Kokkonen stresses, “and that is precisely why the focus on cybersecurity is paramount”.